Home » Posts tagged 'altcoins'
Tag Archives: altcoins
MENTORSHIP ADVISORIES


https://www.amazon.com/author/alfredmbati
Follow the Diplomatic Lifestyle channel on WhatsApp:
https://whatsapp.com/channel/0029Va6g8eOBVJl8owuTEW30
Increasing tax doesn’t necessarily increase tax collection since tax collection is tied to revenue generation. Added taxes means less consumption, less revenue generation & consequently less tax collection:
When leaders prioritize personal gain over the welfare of those they’re elected to serve, the result is a perversion of the leadership mandate. It’s detrimental to the faith of the electorate. Let’s remember, business acumen and leadership are distinct entities.
Practicing resilient leadership means you’ll project a positive outlook that will help others maintain the emotional strength they need to move forward and overcome setbacks.
Issuing directives past midnight shows a lack of capacity in decision-making, creating cataclysmic sectoral confusion :
When disciplined forces of different cadres wrangle indecently in public view, there lies a problem with command structures & communication. The bosses are sleeping on the job:
Tesla’s Cybertruck, touted for its rugged design, faces a bizarre setback at a car wash. After a wash, the 6,600-pound truck can shut down, rendering its console blank and transforming it into a giant metal brick.
Despite its intended off-road prowess, the vehicle may struggle with mundane tasks. Tesla advises against washing the truck in direct sunlight to prevent corrosion, and offers a special “Car Wash Mode.”
“Failure to put Cybertruck in Car Wash Mode may result in damage,” the company’s manual reads. “Damage caused by car washes is not covered by the warranty.”
When sadists regimes who have never been entirely for the people are guilty of Dialing Up the Misery of the Citizens so they can push unpopular policies on distracted citizens only to miraculously & heroically end the same :
In the church “industry”, when a rival church opens near a dominant church, they stand near the gate of the dominant church with fliers inviting the faithfuls to their new church. Instead of going to look for lost souls, they want those already in another church, maybe same hereditary
Systems work when there is order. The leaders in power know that very well; so they promote a disorderly community. They have capitalized on that as the gains are hefty:
When things aren’t going your way, then you have to force them to go your way by stifling any obstacles therein by all means necessary:


GREAT WALL OF CHINA LESSONS
When the Chinese decided to live in peace, they built the great Wall of China. They thought that no one could climb it because of its height…
However, in the 100 years after its construction, the Chinese were invaded 3 times more.
Enemy infantry soldiers never had the need to climb or penetrate the wall.
Because they always bribed the guards and got in through the gates.
The Chinese had built high and thick walls; But they couldn’t build the characters of the wall guards.
As a result, building human character is different and important…
It precedes the construction of everything else.
This is what the new generation needs today.
As an orientalist said; “If you want to destroy the civilization of a nation, there are three ways;
- Destroy the family structure.
- Destroy the education system.
- Belittle and demean their role models and references.” To destroy the family; Belittle and degrade motherhood. To destroy the education system; Do not give importance to educators and teachers and lower their reputation in society so that their students will despise and belittle them.
- Belittle the reputation of role models.
- Work insidiously to destroy scholars and scientists, so that they are suspected and no one listens to them or follows them…
When the conscious mother is lost, dedicated teachers are lost and role models are discredited. Who will teach HUMAN VALUES to young people… ??

BITCOIN BLOCK REWARDS HALVING TIMELINES ⏳⛏
The Bitcoin halving is a significant event that occurs approximately every four years, reducing the block reward for miners by half. This deflationary mechanism is designed to control the issuance of new bitcoins and mimic the scarcity and value preservation of precious metals like gold.
The timeline begins in 2010 with the original reward of 50 BTC per block. We’ve experienced several halvings since then, with the reward decreasing to 25 BTC, and then to 12.5 BTC. Currently, we are in the era of 6.25 BTC rewards per block. Future halvings will further reduce the reward to 3.125 BTC, and eventually to less than 1 BTC per block as we approach 2040.
This reduction in supply issuance theoretically increases scarcity and has historically preceded significant price increases for Bitcoin. The cap of Bitcoin’s total supply is set at 21 million coins, ensuring that the asset remains scarce and deflationary, contrasting with traditional fiat currencies susceptible to inflation.

CLICK HERE TO GET THE PRINT BOOK AND EBOOK FOR SOME MORE INSIGHTFUL READING.
DAILY QUOTES

Follow the Diplomatic Lifestyle Journal channel on WhatsApp:
https://whatsapp.com/channel/0029Va5vOub7DAWxFS8ck509
The police & military should prioritize cooperation & collaboration in the interest of maintaining law & order. Violence between security forces is counterproductive & sets a dangerous precedent.
Understanding Bitcoin’s Ecosystem 🌐💡
A quick glance at the Bitcoin ecosystem reveals a dynamic flow from concept to operation. It begins with an idea, which materializes into code. This code establishes the protocol that connects a network of nodes, essentially the infrastructure that supports the digital currency’s operation.
Participants in the network, known as Bitcoiners, safeguard this protocol. Their collective agreement, or consensus, is pivotal in upholding the network’s values. This shared consensus generates markets, enhancing Bitcoin’s functionality as a currency.
In return, these markets incentivize the community, rewarding their contribution and investment in the system. Thus, the ecosystem of Bitcoin is a self-reinforcing cycle of innovation, protection, and growth, contributing to its viability as a decentralized financial system.
Casting the government as the creator & solver of economic distress highlights a choreography designed to reshape narratives & to manufacture consent when the underlying issues remains in question:
When you aid in concealing the truth from the public through manipulating information & how its presented while shamelessly taking pride in it
When religion is all about mastering the art of crowd control, then having a bare minimum knowledge in religion tends to set up unsuspecting people to be swindled in a religious set up.




CODEX OF PRINCIPALITIES AND POWERS


https://www.amazon.com/author/alfredmbati
The effect of corruption on a country where foreigners can mistreat locals , knowing they can get away with anything , & locals can’t fight back because they fear not earning a dime.

Encounter Driving:
We have commercialized everything including life, people & those entrusted with protecting others as we develop an appetite for money. Money is now the goal & poverty is the enemy. Having money as the equation of our lives makes us see who we exactly are & are becoming :
In life, there exists a privilege to conceal things and it’s your privilege to discover them. No one can discover the height of heaven, the depth of the earth or all that goes on in your mind. However, if you remove obstacles and irrelevancies that come your way, you will be able to rightfully craft your trade & be able to master, rule and subdue over the universe and/or desired jurisdiction with wisdom. Wisdom that will enable you to know that timely advice and valid criticism is always treasured by the one who needs it.
The future belongs to those who know where they belong:
The idea of entering an operation room without personal protective equipment when an operation is ongoing irrespective of who you are is professionally unethical:
When history is an accumulation of guesses, selectively passed down through well meaning flawed processes . We will most likely NEVER know in-spite of saddening it is:
When things aren’t going your way, then you have to force them to go your way by stifling any obstacles therein by all means necessary:
Beware when entities don’t care about what you think & don’t have your best interests at heart:
Beware when entities don’t care about what you think & don’t have your best interests at heart:
As you go about in life, beware of cheap or free offers as they can be terrible since no business is free:
The drive after Super Tuesday encounters:
IED SAFE DISTANCE REFERENCE CHART

A hunter always kills its prey while a tracker understands the prey:
All revelations seem impossible until they are inevitable:
Don’t follow where the path may be, go instead where there is no path & leave a trail:
In the world of propaganda, the truth doesn’t matter :
Whenever someone is accused of something, they will use it as an accusation & have nothing else to say/add while tampering with evidence:
Beware when you are only interested in price interests & then forget production since you prioritize borrowing at higher interest rates to pay lower interest rate debts:
If you can’t find true love. WORK HARD MAKE MONEY & enjoy your SINGLE life in peace. Nobody has ever died from being single but so many have died for being with the wrong partner. Life has worth more, than waste your time with the wrong person
The irony when the entity that you hindered to head a department, institution or state succeeds to head a regional institution superior to what you hindered:
When you take action without making sure what action was needed, that action will lead you into a disaster:
EXCLUSIVE VALENTINES MUST READ since Seduction can be overpowering.
✅ The World’s Most Dangerous Drugs & Poisons
✅ Wealth Trading
✅ Natural Waters Swimming Risk Factors
🔵 The Art of Stewardship
🔵 Presidential, VIP, Diplomatic Protection & Security
https://www.amazon.com/author/alfredmbati
When the ones deciding & making rules don’t depend on a system as He/she is free from it & therefore he/she doesn’t feel the pain like the rest of the people then expect ridiculous regulations to be curated:
Delving into the obsolescence of social networking sites while heralding the rise of social interaction sites thanks to web 4.0 Only a captain of Serendipity will watch the tide:
Devising a strategy to create bottle necks in the system to justify the push for a private entity to be contracted to provide a service. When the plan goes through, the cost of acquiring the service will triple unless it’s stopped in advance:
When the elites use state resources to buy expensive assets & to finance their lifestyle while moving around with millions in events only to claim being broke & to wants others to contribute for disasters is a real fallacy !
Creating a pattern of impunity for the wealthy, where the impoverished are used as a scapẹ́goat while the wealthy manipulate systems to evade consequences :
✅ RULES OF INVESTMENTS: ✅
1. ALL INVESTMENTS COME AND GO. INVEST WISELY AND WHAT U CAN AFFORD TO LOSE.
2. NEVER TAKE LOANS TO INVEST. INVEST IDLE MONEY.
3. KEEP PROFITS, MAINTAIN CAPITAL.
4. DON’T BE SELFISH.
5. LEARN TO BE DISCIPLINED.
The habit of saying things and doing the exact opposite with confidence is hallucination & Delusional:
Half truths always distort the full picture, which manifests itself when the other half isn’t silenced. Act of manipulating facts & shaping public opinion. Turning dreams into nightmares:
It’s hard for a nonbeliever to believe that which looks like a fallacy when it looks so unreal & you can’t explain what it is & how to resolve it based on scientific paradigms:
Money, power, status etc. isn’t made in ordinary transactions but in dealings engineered by emergencies & crisis to avoid set guidelines, procedures etc.
The establishment of an After School Satan Club, despite opposition from faith & education leaders in Tennessee, could be a controversial development. It’s essential to understand the reasons behind such opposition & the implications for the educational landscape.
Beware of decisions that places individuals (collectively) in a precarious position due to perceptions that a government agency can exhibit partiality in determining an entity’s entitlement to seek redress while elevating certain individuals, takes precedence over its main duty of impartial service:
Bitcoin, Altcoins, Crypto Currency And Block Chain Technology

Bitcoin, Altcoins, Crypto Currency And Block Chain Technology
By Alfred Mbati | sanfordestroecompany@gmail.com
The most disruptive and revolutionary Inventions or Innovations always come from the extremes and not from corporate circles. Inventors always view things differently. They always see the big picture. As a result, they end up creating new Products / Services and entire systems that revolutionize the world. It is for these particular reasons that Crypto Currencies and the Block Chain Technology were invented. Crypto Currency is virtual or digital money that is being created, stored and exchanged on networks, which have computers that are connected on the internet. Crypto Currency is digital currency that has been designed to operate in a way that is devoid of the Central Bank, Reserve Bank, Political or Individual Control. The ultimate power of Crypto Currency has been able to be seen through its mainstream adoption and an ever-growing value of its adoption. Crypto Currency was invented as a way disinter-mediating Governments and Banks / Financial Institutions from manipulating money. A detailed Article on how this is done is explored in the Diplomatic Lifestyle Journal December 2016 Edition: Money Skewing Schematics Article.
HOW DOES CRYPTO CURRENCY BLOCK CHAIN TECHNOLOGY WORK?
A Crypto Currency is an entry on a publicly or privately distributed computer called a Block Chain. The Crypto Currencies Ledger is its Block Chain. A Block Chain is a record of every Crypto Currency that is in existence; including every Crypto Currency Transaction, that has ever taken place on the Crypto Currency Network. The Crypto Currency Chain always balances as no Crypto Currency ever leaves the chain. Banks or Financial Institutions always record Debit and Credit Accounts as a Plus (+) or Minus (-). Banks or Financial Institutions also record their Clients Account as a Digital Wallet. A Crypto Currency is usually sent from one user to another as code. The code that is sent to the new Crypto Currency Owner always acts as his or her new key. As transactions are being constantly processed on the Crypto Currencies Globally shared Network, these transactions are simultaneously synchronized on the one Ledger that is used across the Crypto Currencies Global Network. Each Computer or Crypto Currency minor has a complete and identical copy of the Ledger for referencing purposes. By making the Block Chain to be public, no one person or computer is able to control it. Owners of any network computer who allow their computers to be used for processing a transaction and for keeping the network secure are automatically rewarded with a fraction of the processed Crypto Currency as Transactional Costs. This enables them to replace Financial Institutions, Banks or Bankers.
The Transactional Cost payments may be capped at a maximum amount. When the capped payment amount has been reached for the day, further transactions processing by the owners network computer may be undertaken for free e.g. Bitcoin initially limits each processing machine to 1800 Bitcoins Per Day. This is what is referred to as Mining in the Crypto Currency world. Crypto Currency payments can be directly sent from one entity to another without having to pass through a Trusted Third Party by a peer-to-peer network. This peer-to-peer network is also used to prevent double spending. Digital Signatures are also used to prevent double spending. In addition, the network automatically timestamps transactions by hashing them into an existing chain of a hash-based proof of work. As a result, a record that cannot be changed without redoing the proof of work is formed. A Hash Function is any function that is used to map an arbitrarily sized data to a fixed size data. Hash functions accelerate searches in tabular data or in databases by detecting duplicated records in a large file.
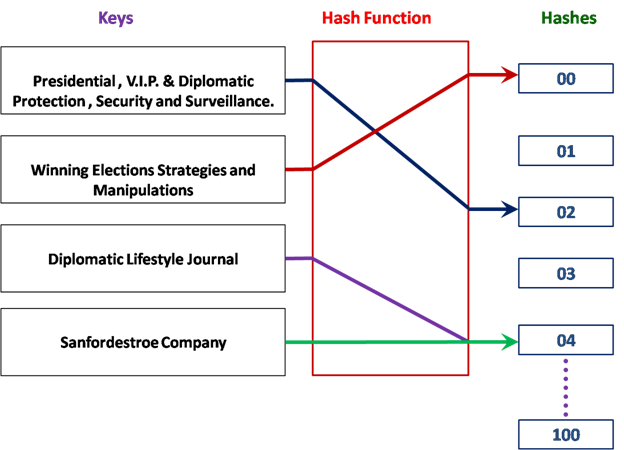
Diagram showing a Hash Function that maps Entities to Integers from 0 to 100.
There is a collision between Keys.
CLICK HERE TO GET THE PRINT BOOK AND EBOOK FOR SOME MORE INSIGHTFUL READING.
Here are the Hinmam Document Exhibits 1 and 2 on cryptocurrency malpractices for download in pdf :
hinman-exhibits-by-number-part-1-1.pdf
hinman-exhibits-by-number-part-2.pdf

WORLDCOIN COMMENTARY
The negativity surrounding Worldcoin stems from concerns about its proof-of-personhood technology, worries about potential market manipulation, and tokenomics. Significant amounts of Worldcoin supply are controlled by insiders and market makers. This has led to suspicions that early participants may be at risk of losing value, especially given the large circulating supply and the potential for market manipulation. It’s therefore summed up as A revolutionary proof of personhood, The beginning of a new dystopian world order and A scam to exchange sensitive personal information for a shit coin.
This Worldcoin cryptocurrency will make very many subscribers regret their decision to register with them because they do not read the Terms & Conditions and Privacy Policies of websites. Worldcoin uses an Open Source software. Their Terms & Conditions states that they cannot prevent people from getting scammed in the name of Worldcoin. Of concern is that World Coin is illegal in the USA.
Some of their terms & conditions:
– You shouldn’t be a US Citizen.
– You shouldn’t be living in the US.
– You cannot sell that coin to a US citizen.
With all that information, many people especially from Africa are lining up at Worldcoin stations to get their eyeballs scanned. Worldcoin also started by setting up sign-up stations in 4 European countries:
1. Germany
2. The U.K
3. France
4. Spain
Privacy regulators in the first three of these countries have already raised eyebrows.
DATA PROCESSING Data & GDPR
Worldcoin claims consent is their legal basis for processing, but there’s some suspect practices in play:
• They incentivize users to sign-up for free crypto
• Worldcoin’s tech developers are for-profit ≠ Worldcoin Foundation is non-profit
It remains to be seen how this AI/crypto endeavor will navigate the complexities of EU regulations and those countries that are or will be overtly questioning Worldcoin’s data practices. Many countries are either currently investigating the company or are in the process of investigating the company, while particularly focusing on the legality of collecting and storing biometric data.
If you consent to the Biometric Data Consent Form and enable ‘data custody’ you allow Worldcoin to do the following with your Biometric data:
1. Hold on to the image data collected by the orb during the field test;
2. Send the data to their teams in European Union and USA;
3. World coin uses the image data to continue ‘training’ their software. In this context, ‘training’ means using your image to learn the software learn or distinguish non-human and differenciate you from your mother.
4. Your data is used to test and evaluate personnel who work on the system.
5. Your data is used to develop and train and algorithm to differentiate among images of human irises and faces.
6. Once they have your iris and facial images, the data will be used to develop, train and test a system to detect wether a user is a human presenting a real human eye or wether the sign up is valid.
Lastly, World coin can never sell your data. They just don’t guarantee it. That’s the risk.
REMEMBER THE First rule of crypto is NEVER attach a real life identity to your reference environment on the blockchain.
CLICK HERE TO GET THE PRINT BOOK AND EBOOK FOR SOME MORE INSIGHTFUL READING.

BITCOIN BLOCK REWARDS HALVING TIMELINES ⏳⛏
The Bitcoin halving is a significant event that occurs approximately every four years, reducing the block reward for miners by half. This deflationary mechanism is designed to control the issuance of new bitcoins and mimic the scarcity and value preservation of precious metals like gold.
The timeline begins in 2010 with the original reward of 50 BTC per block. We’ve experienced several halvings since then, with the reward decreasing to 25 BTC, and then to 12.5 BTC. Currently, we are in the era of 6.25 BTC rewards per block. Future halvings will further reduce the reward to 3.125 BTC, and eventually to less than 1 BTC per block as we approach 2040.
This reduction in supply issuance theoretically increases scarcity and has historically preceded significant price increases for Bitcoin. The cap of Bitcoin’s total supply is set at 21 million coins, ensuring that the asset remains scarce and deflationary, contrasting with traditional fiat currencies susceptible to inflation.
CLICK HERE TO GET THE PRINT BOOK AND EBOOK FOR SOME MORE INSIGHTFUL READING.

THE FINANCIAL EMPOWERMENT OF BITCOIN OVER FIAT. 💰🔋
The debate between the preservation of financial energy in fiat currency versus Bitcoin is increasingly relevant. Fiat money, subject to inflationary pressures, often sees its purchasing power erode over time. As central banks have the authority to print more money, the individual’s hard-earned income could lose value, metaphorically speaking, like a battery draining its charge.
Bitcoin offers a contrasting financial narrative. It operates on a deflationary model with a cap of 21 million coins that will ever exist, enforced by unalterable code. This scarcity is similar to charging a battery to full capacity, suggesting the potential to maintain or increase value as opposed to the depreciating nature of fiat currencies.
This fundamental difference is why some investors and economists argue that Bitcoin can act as a store of value, potentially safeguarding financial energy against the gradual loss encountered with traditional currency systems.
CLICK HERE TO GET THE PRINT BOOK AND EBOOK FOR SOME MORE INSIGHTFUL READING.

TRACING BITCOINS HALVING HISTORY ⛏🕒
Every four years, Bitcoin experiences a pivotal moment known as “halving,” where the number of bitcoins awarded to miners for adding new transactions to the blockchain is slashed by half. This deflationary event is a core mechanism designed to mimic the extraction of a finite resource, akin to mining gold.
Starting off in 2009, miners received 50 bitcoins per block. The first halving in 2012 brought this number down to 25. Fast forward to 2016, and the reward halved again to 12.5 bitcoins. The most recent halving in 2020 saw the reward decrease to 6.25 bitcoins per block, making the minting of new bitcoins even rarer.
As we approach the next halving in 2024, miners will see their rewards for securing the network drop to just 3.125 bitcoins per block. Each halving event subtly underscores the scarcity of Bitcoin and is often surrounded by increased discussion about its potential impact on the cryptocurrency’s valuation and miner ecosystem.
CLICK HERE TO GET THE PRINT BOOK AND EBOOK FOR SOME MORE INSIGHTFUL READING.

Diplomatic Lifestyle Journal September 2017 Edition Article Reviews
PRESIDENTIAL, V.I.P, AND DIPLOMATIC PROTECTION, SECURITY & SURVEILLENCE Written for DIPLOMATIC LIFESTYLE JOURNAL September 2017 EDITION| diplomaticlifestyle@gmail.com
Your security starts with you. If you choose to stay ignorant and happy then be very weary. It is better to stay informed and always alert /cautious for any unexpected eventualities. Moreover, if you are not able to win a battle, then do not fight it.
Security is categorized into three areas:
* Economic Security
* Political Security
* Social Security
Your most serious security threat always emanates from Radicalization. Here, your Assailant or Assailants are made to believe that you are an enemy to an ideology / ideologies that they believe in or have been made to believe in. They are then motivated to defeat their enemy (that is you) as that will be of immense benefit to them. The matter worsens when you are seen as a Social Threat, Economic Threat or Political Threat that needs to be eliminated. Your Killer’s Official Elimination Policy may be based on the principal that the branches of a tree should be cut off instead of the trunk in order for them to succeed. With this principal, they will ensure that every heir to your Social, Economic or Political throne is killed / eliminated to create a hiatus when you die , when they finally kill you or get rid of you. This principal is always used in situations where there is an Inheritance Policy that passes Wealth or Power down to the First Born, Family Members or Groomed Successors. Such a scenario always results to a security nightmare, as the Eliminator will always aim at solidifying his or her power. After consolidating his or her power, the Eliminator will then embark on a killing spree to eliminate potential competition threats. As a result, any person that is around you will be very afraid as your Eliminator may decide to kill them to weaken you or to pass an indirect message to you. This Guilt by Association always makes you to always aim for success because if you fail, then everyone else dies (including your family). You should therefore be cognizant of the matter and the dangers therein. Once you are aware of the dangers that you and your associates are facing, the need to put in place proper and tight security measures to all the parties involved arises. For instance, when you are with people, women and Foreign Agents may accompany a Male Agent whereas a Male Agent can be escorted by a mix of Male Agents, Female Agents and Foreign Agents to dupe you from suspecting them as being potential security threats to you. When in reality, they are out to harm you.
When evaluating an Elimination Scheme, always ask yourself what eliminating Person X will benefit Person Y. If there are no benefits, then the fight is personal and not territorial. You should also be able to find out on who or what your intended attacker is working for.
Note: You cannot be able to protect other people if you are not able to protect yourself.
If you want to see the unseen, you must be able to render yourself invisible. This is possible through studying ways that will enable you to hide in plain sight. For example:
* When you use a route to go somewhere, use a different route when returning.
Your Ingress (Entry) Route should be different from your Egress (Exit) Route to
create uncertainty to your Assailants.
* You can wear a big hat or cap that covers much of your forehead. This is always
complemented with sunglasses. By dressing this way, you will be able to conceal
your face to create some form of anonymity.
* If you are Security Conscious, you can use 2 Female Bodyguards or 2 Guards who
have Signal Jammers concealed in their clothing to block (wireless) Security
Cameras.
* You can also make yourself disappear by walking in crowded places while using
regular clothing that does not have shouting colors such as red clothing.
* You can also create a hasty disguise by alternating clothing and clothing colors,
alternating accessories e.g. wristwatch by wrist ankle, alternating messenger bags
with totes, alternating shoes AND by subtracting or adding reading glasses,
sunglasses and hats.
Remember, disguises must be explainable. Fake moustaches etc will result to you
being convicted and jailed.
Your most important Security Principal is to always protect your own people. This is especially true in your home. Your first line of defense is to build a home that:
* Incorporates security features and safeguards against natural calamities such as
hurricanes, typhoons and earthquakes.
* Is self-sustaining incase of limited Supplies.
* Is able to sustain the safety of its occupants.
* Is safeguarded against manmade calamities such as terrorism etc.
Your starting point is to have a Security Guard or Guards at your Gate / Gates or have an Electric Gate that can be remotely opened and closed. This will enable you to avoid dealing with Strangers or Stalkers at your gate. These strangers can be Assassins, Foreign Government Agents, Government Agents, Militia or Mercenaries that have been hired to kill you. Your compound should have a minimum of two Gates and two Compound Divisions. These Compound Divisions include the Outer Perimeter of the Compound and the Inner Perimeter of the Compound. Your Residence is always placed in the Inner Compound Area.
In your Compound, there are 03 Security Measures that must be considered:
* Structured or Physical Security Measures such as enclosing the residence in a
Wall, use of Razor Wire, use of Electric Fencing etc.
* Technological Security Measures e.g. use of Closed Circuit Television, Motion
Detectors, Automated Doors and Windows etc.
* Human Security Measures which essentially involve the use of Human Beings as
Security Guards.
In case the Human Guards are not properly trained, there are staffing problems and there are issues of Cyber Wars where anonymity issues exist, then a breach in V.I.P. Security is always experienced. Cyber Wars Anonymity problems include the Residences Closed Circuit Television being hacked, the Residences Online Automation Systems such as Alarm Activation Systems or Automated Doors and Windows Systems may be breached online etc. Weapons that are being used with Security Personnel should always be with them. On the other hand, Back up Armor should be kept at a secure Armory in an Armory Box from where it cannot be quickly and easily accessed by an Assailant. The first line of defense for a V.I.P.s Residence is the Main Gate. It is advisable to have a minimum of three Guards guarding the Main Gate. This is to enable the Guards to always be two at all times should one Guard be in need of using the toilet, be welcoming / questioning a visitor, be opening the gate etc. Should an Assailant be able to attack one Guard at the Main Gate with a Crude Weapon or even shoot the Guard, then the other two Guards should be able to foil the attack. If there are only two Guards, then the likelihood of the Second Guard being disarmed by an Assailant after the First Guard is attacked is very high. No matter how trained you are, there is always the element of Surprise, Human Element of Laxity and an element of having a Sleeper Cell in your Security Circles that may provide a security flaw in your security undertakings e.g. a Mole or Spy. Should any security flaw be in existence, then your Assailant can use the flaw to fully undertake a Detailed Surveillance of your Property or Residence. He or she can then take a defensive position when attacking. As a result, it will be difficult to neutralize him or her as he/ she will be having a vantage position over you / your Guards as he or she knows:
* What he /she wants.
* Where to get what he /she wants.
* How to get to what he /she wants.
* When to get to what he / she wants.
In the end, you will be caught unawares as you will be playing catch up with the Assailant.
Note: The Security Setting of your Residence can also be replicated on your Office or Company Premises.
Your Residence / Office should be guarded by a Section of at least 09 Officers and their Supervisor/ In Charge, making it a total of 10 Officers who are acting as an Element, Section or Unit. 03 Officers will be Guarding the Main Gate, 02 Officers will be monitoring the C.C.T.V., 01 Officer will be the Guards Deputy Supervisor, 01 Guard will be Guards Supervisor while the other 03 Guards will be patrolling the Premises / will be strategically stationed at Watch Towers as Snipers.
The C.C.T.V. must always be monitored on a 24 hour Basis with its Records Kept / Backed Up at a secure location. The total number of Security Guards will depend on the size of area that they are guarding.
In most cases when you are dealing with a threat of Crowd Attacks, you always do a serious Threat Analysis, Risk Analysis and then determine which Counter Measures or Evasion Techniques shall be put in place. Crowd Attacks can happen in your Residence, While Travelling in between Destinations, During Demonstrations, when at an Event / Specific Location such as your Office or Hotel etc. It is always advisable to note that over relying on Government provided security is never a good idea. Always have your own private Security Detail. Government provided Security Detail could be abruptly withdrawn or recalled to their reporting stations thereby leaving you exposed.
A Diplomatic Passport is also issued at the discretion of the Government of the day and can be withdrawn at will. You should therefore apply for a regular passport by design to let the Government decide if they will issue you with a Diplomatic Passport. Should they withdraw the Passport, you can easily claim to have applied for a regular passport, which they should immediately replace it with. Some people use Dual Nationality to evade such a case where the Government revokes your passport without notice.
Since your private security may not be allowed to be armed, always employ Guards that are well trained in Physical combat e.g. in Karate or Taekwondo. Such Security Guards can be able to use crude and easily available weapons to protect you. For example, a good Darts Man can use kitchen knives as weapons, a Swordsman can use a slasher as an improvised sword, a baseball bat can be used as an improvised baton etc. The Security Guards Supervisor / Commander in Charge always reviews the High Value Personalities Security Plan, Security Situation, Coordinates the Security Detail / Plan and also supervises any crisis that he High Value Personality may find himself or herself in. A Site Plan of the high Value Personalities Residences, Offices or Areas of Operations such as Hotels, Restaurants etc is always created. A High Value Personality Extraction Plan is always engaged should things go awry. For example, a peaceful demonstration can turn out to be violent when hired goons are made to infiltrate the demonstrations or attack the demonstration. This may have been planned intentionally at the knowledge of the Security Forces who may want to use the opportunity as a time of dispersing the demonstrators with brutal force. A long standoff between the Security Officers and Demonstrators may also be expected. You should therefore be always aware of any nebulous connection that is there to deliberately use brute tactics to create chaos, foster discontent among people and to cause disillusions. You may be mistaking peace for quietness when in the real sense there is an evil plan that is taking place in the background.
Always be aware or cognizant on how easy / difficult dealing with a particular situation is. When an attack occurs, what is the appropriate response to undertake? There may be instances where the Security Detail is faced with a Nightmare Scenario where it is difficult for them to defend a High Value Personality.
Even thou a place may be Physically Obstructed, an Assailant / Attacker may manage to breach the Initial Security Perimeter with ease. This may be so if the attack was properly planned.
They may even resort to using a less sophisticated attack approach to prevent the High Value Personality from easily detecting the attack. The Assailant / Attacker can also obtain crucial information from spies or from instructions that may have been given to them by High Level Insider Officials. Always be aware of the fact that your Security Detail may be Used / Hired to kill or eliminate you. Your Security Detail should always have a detailed and continuous security review of your Site Plan. This Site Plan can be the layout of your Residence, Office Location, and Favorite Recreational Facility etc. Ways through which you can be poisoned and the effects of the poisons can be found in the Diplomatic Lifestyle Journal Editions Drug Debunking Articles.
As a Very Important Person, you should always be able to know your security arrangements and patterns. Always employ a mix of security operations or patterns to avoid being predictable and always have a Tactical Retreat Plan should the initial security plan fail. V.I.P. Security Guards and the V.I.P. himself / herself should be able to be highly trained in fighting installation security. As a result, the High Value Personalities Compound / Residence is always divided into several sections in case of a security breach. Each section will then have various security features and high value V.I.P. Surveillance Tools.
In case a V.I.P. Residence, Office etc is attacked, Security Personnel always conduct an overview of the area while using various surveillance methods such as Chopper Patrols, debriefs from Site Personnel / First Responders etc. Remember, your greatest enemy always comes from within. It is therefore imperative that you are aware of the possibility of your security being breached through having insider information being leaked to your enemies. Leaked Security Details, Leaked Top Secret Information and Security Flaws is always a symptom of an essential lack of cohesion between the Parties / Entities involved. Decoy Security Passwords are also good security strategies to use. For example, most Financial Institutions use the Pin Reversal Alert Technique to allow their Clients to call the police in case of distress when withdrawing money from an Automated Teller Machine. In such an instance, the A.T.M. will automatically alert the Financial Institutions Security Team of the A.T.M. Cards security breach and the A.T.M. will dispense the input amount, albeit, it will deliberately withhold the dispensed money in the waiting compartment instead of letting it out to the outside tray ( from where a Client can physically take the money). As a result, the person withdrawing the money will not be able to physically take the money. The A.T.M. Card’s Pin will also be blocked from performing further transactions. At this time, the A.T.M. Camera will be covertly taking pictures of the thief or surrounding for security purposes. The same Pin Reversal Technique can be used in Mobile Money Transfer, Home Security Systems, and Vehicle Security Systems etc.
A Security Guard can also fool his /her Assailants that he / she is in the company of a team of Security Officers by shooting at the Assailants with different ammunitions, from different locations. This can fool someone to think that the shootings are from different people.

In case of a Security Breach or Ambush:
* The first duty of any V.I.P. Security Officer is to secure the package (High Value
Individual) in a Safe Haven or Secure Location.
* The Team will then take Tactical Positions while setting up in war formation.
* The V.I.P.s Security Detail will then Identify the Level of Attack and the Position or
Positions of Attack.
* The Next Step will be for the V.I.P. Security Detail to Identify the weapons of attack
and if they have a Security Back Up Team or not. Security Backup is usually
essential especially when you are tactically overwhelmed and there is a need of
immediate assistance. If the Backup Team is not around, then it is always
advisable to assume that you are on your own. This is so, because the Backup
Team can be eliminated while en route to support the V.I.P. Team. The Backup
Team can also be faced with security obstacles that were deliberately put in place
by the attacker to stall or delay their response. As a result, the attacker will have
secured ample time to accomplish his or her mandated mission before the Backup
Team arrives.
* The V.I.P. Security Team will then study their terrain, know their terrain or orient
themselves with the terrain on the go. This is always done in advance but in most
instances, it is never possible with a surprise attack. The information is always
crucial in case of a Tactical Retreat or in identifying potential Security Lacunas
that need to be sealed in advance. No human being is perfect and so, some Security
Flaws are always expected. Security Flaws may also be deliberately made to fool an
Assailant into a Security Trap. It is at this moment that the Security Team has to
consider or decide what will happen in case they find themselves in a Security
Holdout. This is the worst-case scenario, as the team has to employ Multiple
Surveillance Techniques and Security Briefings to determine:
*** How to out-maneuver the enemy.
*** Whether to surrender.
*** Whether to employ Security Delay Tactics as the Backup Security arrives, etc.
It is crucial that you do not always dispatch one Security Backup Team but Multiple
Teams to avoid having a Single Point of Failure.
* Lastly, the V.I.P. Security Detail will constantly identify and monitor the logistics
involved in the Counter Attack, the number of Security / Military Assets involved in
the counter Attack, the ammunition that the Security / Military Assets have, the
Defense and Attack Limitations or Vantage points etc. This will be considered as a
way of ensuring that the High Value Person is safely kept out of danger.
Note: As a V.I.P., it is essential that you acquaint yourself with Self Defense Tactics or Techniques, as they will help you to survive an attack. For instance, training on how to jump out of a moving vehicle or onto a moving vehicle.
To create anonymity, an amorphous Team of Security Personnel can be set up to eliminate or neutralize you. This team always consists of newly trained recruits who can be quickly assembled to perform a task. Once the task is accomplished, they will be deployed to their assigned positions (in different postings) to create anonymity and an opportunity of foolproof deniability. Since allegations must be confirmed to be true with shreds of evidence, such an assembled team can never be found.
BITCOIN, ALTCOINS, CRYPTOCURRENCY AND BLOCKCHAIN TECHNOLOGY. Written for DIPLOMATIC LIFESTYLE JOURNAL September 2017 EDITION | diplomaticlifestyle@gmail.com
The most disruptive and revolutionary Inventions or Innovations always come from the extremes and not from Corporate Circles. Inventors always view things differently. They always see the big picture. As a result, they end up creating new Products / Services and entire systems that revolutionize the world. It is for these particular reasons that Crypto Currencies and the Block Chain Technology were invented. Crypto Currency is virtual or digital money that is being created, stored and exchanged on networks, which have computers that are connected on the internet. Crypto Currency is digital currency that has been designed to operate in a way that is devoid of the Central Bank, Reserve Bank, Political or Individual Control. The ultimate power of Crypto Currency has been able to be seen through its mainstream adoption and an ever-growing value of its adoption. Crypto Currency was invented as a way disinter-mediating Governments and Banks or Financial Institutions from manipulating money. A detailed Article on how this is done is explored in the Diplomatic Lifestyle Journal December 2016 Edition: Money Skewing Schematics Article.
HOW DOES CRYPTO CURRENCY BLOCK CHAIN TECHNOLOGY WORK?
A Crypto Currency is an entry on a publicly or privately distributed computer called a Block Chain. The Crypto Currencies Ledger is its Block Chain. A Block Chain is a record of every Crypto Currency that is in existence; including every Crypto Currency Transaction, that has ever taken place on the Crypto Currency Network. The Crypto Currency Chain always balances as no Crypto Currency ever leaves the chain. Banks or Financial Institutions always record Debit and Credit Accounts as a Plus (+) or Minus (-). Banks or Financial Institutions also record their Clients Account as a Digital Wallet. A Crypto Currency is usually sent from one user to another as code. The code that is sent to the new Crypto Currency Owner always acts as his or her new key. As transactions are being constantly processed on the Crypto Currencies Globally shared Network, these transactions are simultaneously synchronized on the one Ledger that is used across the Crypto Currencies Global Network. Each Computer or Crypto Currency minor has a complete and identical copy of the Ledger for referencing purposes. By making the Block Chain to be public, no one person or computer is able to control it.
Owners of any network computer who allow their computers to be used for processing a transaction and for keeping the network secure are automatically rewarded with a fraction of the processed Crypto Currency as Transactional Costs. This enables them to replace Financial Institutions, Banks or Bankers.
The Transactional Cost payments may be capped at a maximum amount. When the capped payment amount has been reached for the day, further transactions processing by the owners network computer may be undertaken for free e.g. Bitcoin initially limits each processing machine to 1800 Bitcoins Per Day. This is what is referred to as Mining in the Crypto Currency world. Crypto Currency payments can be directly sent from one entity to another without having to pass through a Trusted Third Party by a peer-to-peer network. This peer-to-peer network is also used to prevent double spending. Digital Signatures are also used to prevent double spending. In addition, the network automatically timestamps transactions by hashing them into an existing chain of a hash-based proof of work. As a result, a record that cannot be changed without redoing the proof of work is formed. A Hash Function is any function that is used to map an arbitrarily sized data to a fixed size data. Hash functions accelerate searches in tabular data or in databases by detecting duplicated records in a large file.
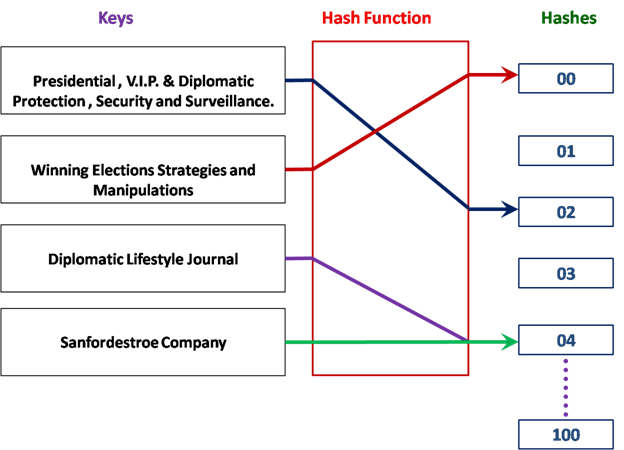
Diagram showing a Hash Function that maps Entities to Integers from 0 to 100.
There is a collision between Keys “Diplomatic Lifestyle Journal” and “Sanfordestroe Company”.
A Hash Function needs to be collision resistant, by ensuring that no data is able to generate the same Hash Value as aforementioned.
In Crypto Currency, the Timestamp Server Work automatically Hashes a block of items that need time stamping. All Data must have a Hash and the Hash is widely published across the entire network.
ADDICTION EXPLOITATION AND CARTELS Written for DIPLOMATIC LIFESTYLE JOURNAL September 2017 EDITION | diplomaticlifestyle@gmail.com
It is always amazing at the way society tends to tolerate the Biggest Killers and Gateway Addictions for people just because they love the Addiction. On the other hand, the same Society always tends to act horrified by much Smaller Destructive Behaviors, because they disapprove of them. Addiction Exploiters always take advantage of this by making deals with Pushers or Sellers to flood the Commodity / Service to the Markets. These Pushers or Sellers may be Doctors who prescribe their drugs to Patients who in turn get addicted to it or Politicians who protect the Addiction Exploiters etc. When money is exchanged to make deals with powerful Decision or Policy Makers such as Politicians, Doctors, Drug Companies etc., Action is always taken after the damage is done and not before the damage is done. Such an Action is always a day late, Short of money and At the expense of human life. Addiction Products or Services always come in the form of Obsessions or Radicalizations e.g. Alcoholism, Cigarette Smoking, Usage of Drugs such as Cocaine / Opioid / Heroin etc. People facilitate Addiction Problems, when they are not willing to work in order to have Food, Shelter and a few luxury items.
NB: There is nothing in life that is free as someone else has to pay for it or is paying for it.
Addiction Cartels always create a problem that makes them money. They also come up with a solution to the problem that they had created and in turn make more money out of it.
SO HOW IS THIS DONE?
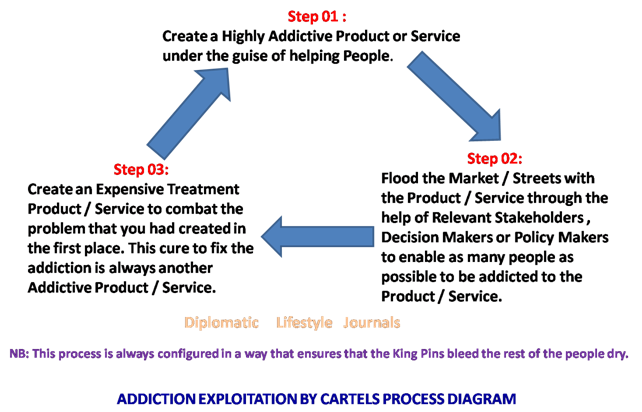
Addiction Exploiters always get away with their crimes because every Country always has two sets of laws in place:
* The Law that favors the Rich or The 1%
* The Law that caters for everyone else or The 99%
Every Political, Economic and Social Spheres of life have been permeated by the Pay to Play Lobbying System. With the right amount, Addiction Exploiters are able to circumnavigate existing systems for personal gain. It is for this reason that Drug Companies are allowed to work on new drugs that will help prevent fatal overdoses when the Users feel like it is okay to overdose themselves. This should not be the case as the Addictive Drug should be completely eliminated. If you did not need the drug before, then why do you need the drug today? Addiction Exploiters always oppose such an action, as they are able to enrichen themselves when more and more people Use or Consume their Products or Services to the point of being addicted to them. This Pay to Play Lobby System enables Politicians and Government Officials to allocate more money to the treatment and cure of a Level 02 Drug instead of a Level 01 Drug. This may be deliberately done, as they profit more from such an arrangement since a Level 01 Drug is actually more dangerous when compared to a Level 02 Drug.

DRUG DEBUNKING Written for DIPLOMATIC LIFESTYLE JOURNAL September 2017 EDITION | diplomaticlifestyle@gmail.com
Sarin is a poison that can be delivered as a Binary Agent. Binary Agents are delivered as two separate components. When the two components are combined, they form a lethal poison. Sarin is a colorless, organophosphorous liquid, which has almost no odor in its pure state. This Nerve Agent or Gas was developed but was never used by Germany during World War 02. German Researchers at I.G. Farben developed a man made chemical know as Sarin in 1938 for use as a pesticide. The Chemical Weapons Convention banned the use of Sarin Gas in 1993. Sarin is used as a Chemical Weapon due to its extreme potency as a Nerve Agent.
Sarin is made from Methlyphosphonly Difluoride and Isopropyl Alcohol and it easily decomposes into Non Toxic Phosphonic Acids when exposed to high PH Levels. It also has a very high Volatility Level, which means that it can easily vaporize from liquid to gas.
SARINS PERCENTAGE COMPOSITION BY MASS.
* Carbon ———- 13.043 %
* Hydrogen ——- 1.087 %
* Fluorine ——— 19.565 %
* Phosphorous — 48.913 %
* Oxygen ———- 17.391 %
HOW DOES SARIN WORK?
A Single Droplet of Sarin is absorbed into the bloodstream when it is inhaled or during contact with the skin. It then paralyses the nervous system by preventing nerve endings from allowing muscles to stop contracting. This usually leads to respiratory failure as the muscles that control breathing are rendered ineffective, resulting to asphyxiation or suffocation. Once the victim has been incapacitated, death is always imminent. Sarin’s ability to mix with water usually enables it to be used as a poison. As a result, ingestion of contaminated Food, Water or Liquid, including light skin contact is possible. All you need is a very small amount of Sarin to cause some devastating harm to your victim e.g. death or permanent neurological damage.




